How much is the phish?
What a month!
As soon as we went live and started getting user traction, we at once.to got confronted with an unexpected problem.
Pretty soon we’ve discovered that our super-fast, super-convenient short links were actively used by phishers.
1e.to is NOT dangerous!
once.to’s URL shortener is free and extremely simple to use, even for an anonymous user: just paste your URL, click Shorten! — bang! — you’ve got a short link on the 1e.to domain.
This ease of use was in a sense playing against us: in a short while we’ve received more than a hundred links leading to all kinds of dangerous, mostly phishing, sites. They were duly reported to Google Safe Browsing, which at one point lead to wrongly flagging the whole of 1e.to as deceptive or dangerous — a very unpleasant development indeed.
It was still possible to navigate past this awful red screen by clicking on “Details” and then “visit this unsafe site”:
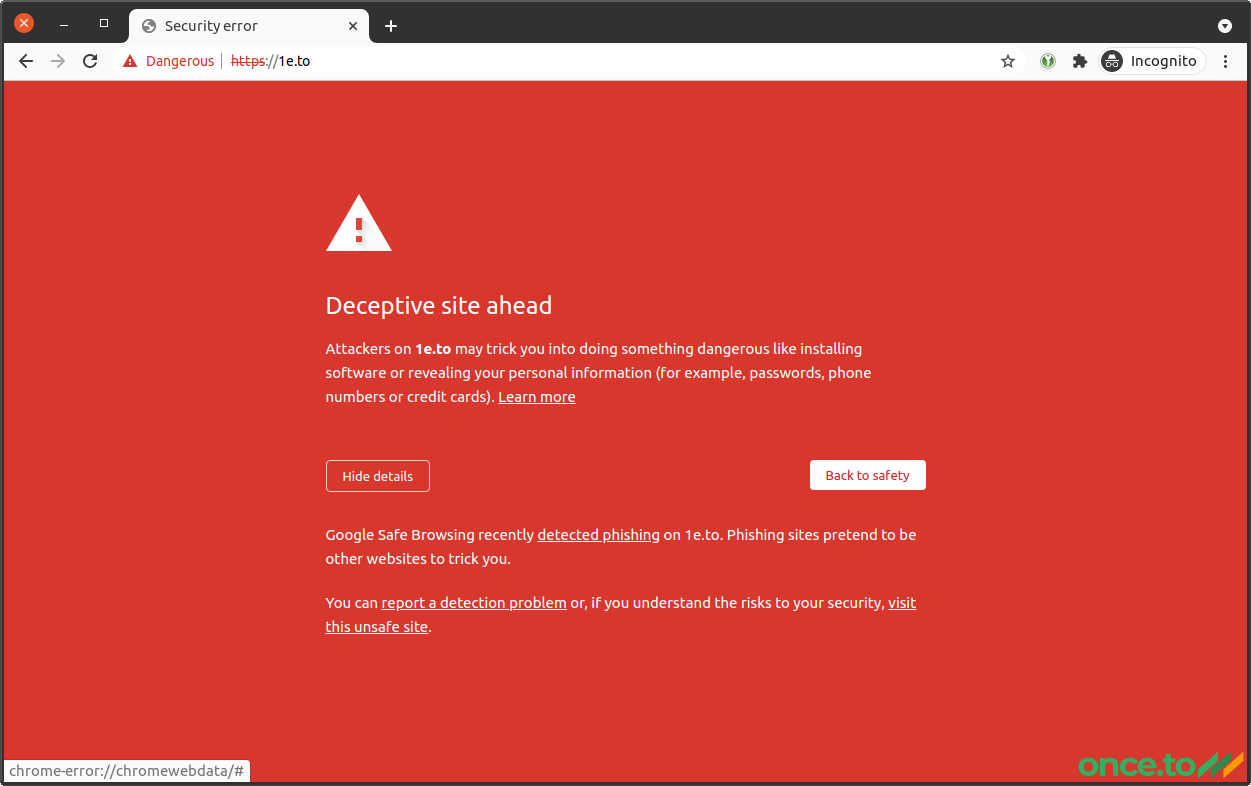
However, you can imagine no one would want to use our short links if they had to deal with this.
Obviously, every malicious link was swiftly taken down, and we’ve been soon cleared by Google Safe Browsing, phew! But the original problem was not solved just yet.
Fighting scammers
Lessons were learned, so we’ve introduced a few initial measures in our and our users’ defence.
Firstly, we created a very easy and effective banning mechanism for users and links, allowing to ban either of them with a single click. This is coupled with a regular checking routine verifying every submitted link. We’re applying a zero-tolerance policy to scam and phishing, so any user submitting a link poiting to a phishing website gets banished from once.to, effective immediately.
Secondly, we introduced URL and domain blacklisting. We’ve discovered that phishers often try to fool users (or maybe detection algorithms) by extending the link redirection chain: making a short link on one URL shortener service, then submitting it to another. This seems pretty desperate as such a redirection chain is all but useless when it comes to algorithms. On the other hand, it helped us to easily identify many malicious URLs.
Likewise, dynamic DNS services allowing to create new third-level domains for free seem to be attractive to scammers, and there’s a similar trend with free website constructors.
All of the above is no problem anymore, because we’ve effectively forbidden other URL shorteners and dynamic DNS services. We just don’t accept them.
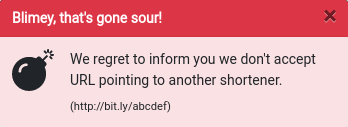
Of course, not every malicious or vulnerable domain is on the blacklist, so it keeps growing.
Thirdly, we’ve integrated Google reCAPTCHA, which has to be solved by every anonymous user trying to shorten a URL with once.to.
Scammers often use VPN and/or proxies when they set up their websites, and reCAPTCHA gets very suspicious when someone tries to operate from such a public address.
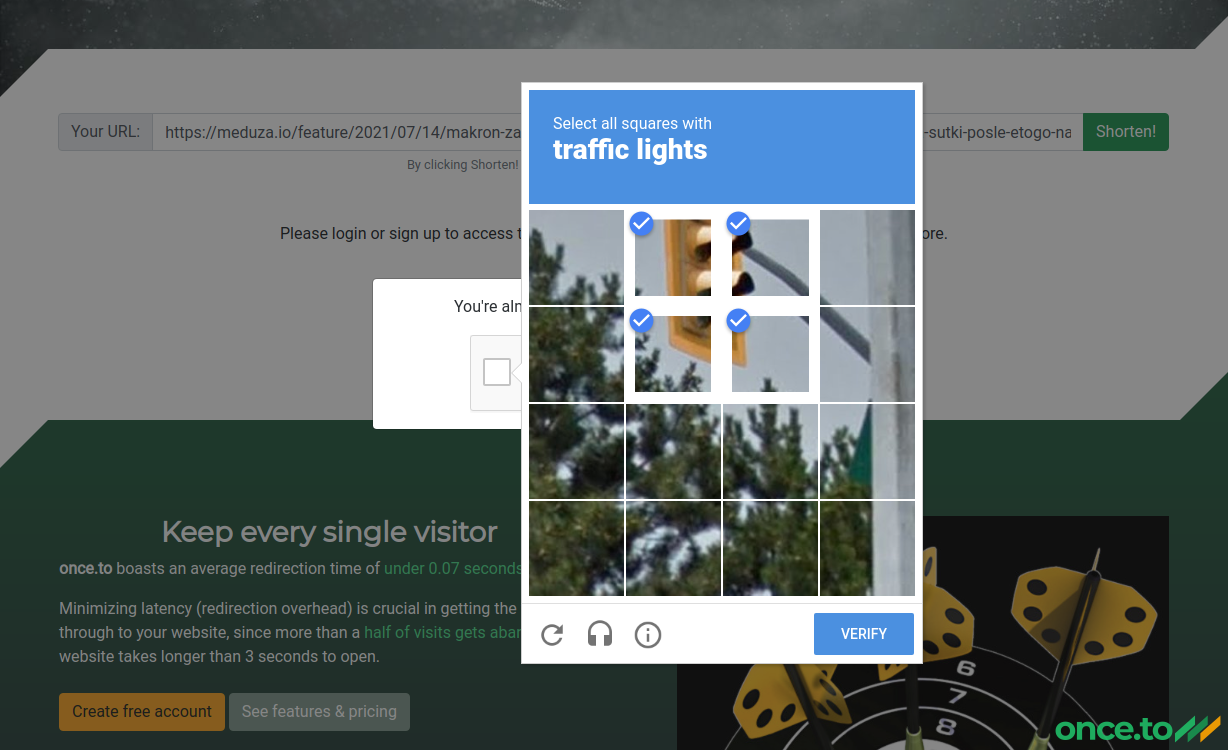
On the bright side, a registered user will never see the CAPTCHA (as we have other means to fight those abusing the service).
Moving on
once.to is now clear of any phishing links and the like. Should they occasionally be submitted, they get momentarily taken down.
To better inform our users of the risks (and the work done) we have even introduced a new takedown screen (notice the slogan at the bottom) — use this link to see it in action:
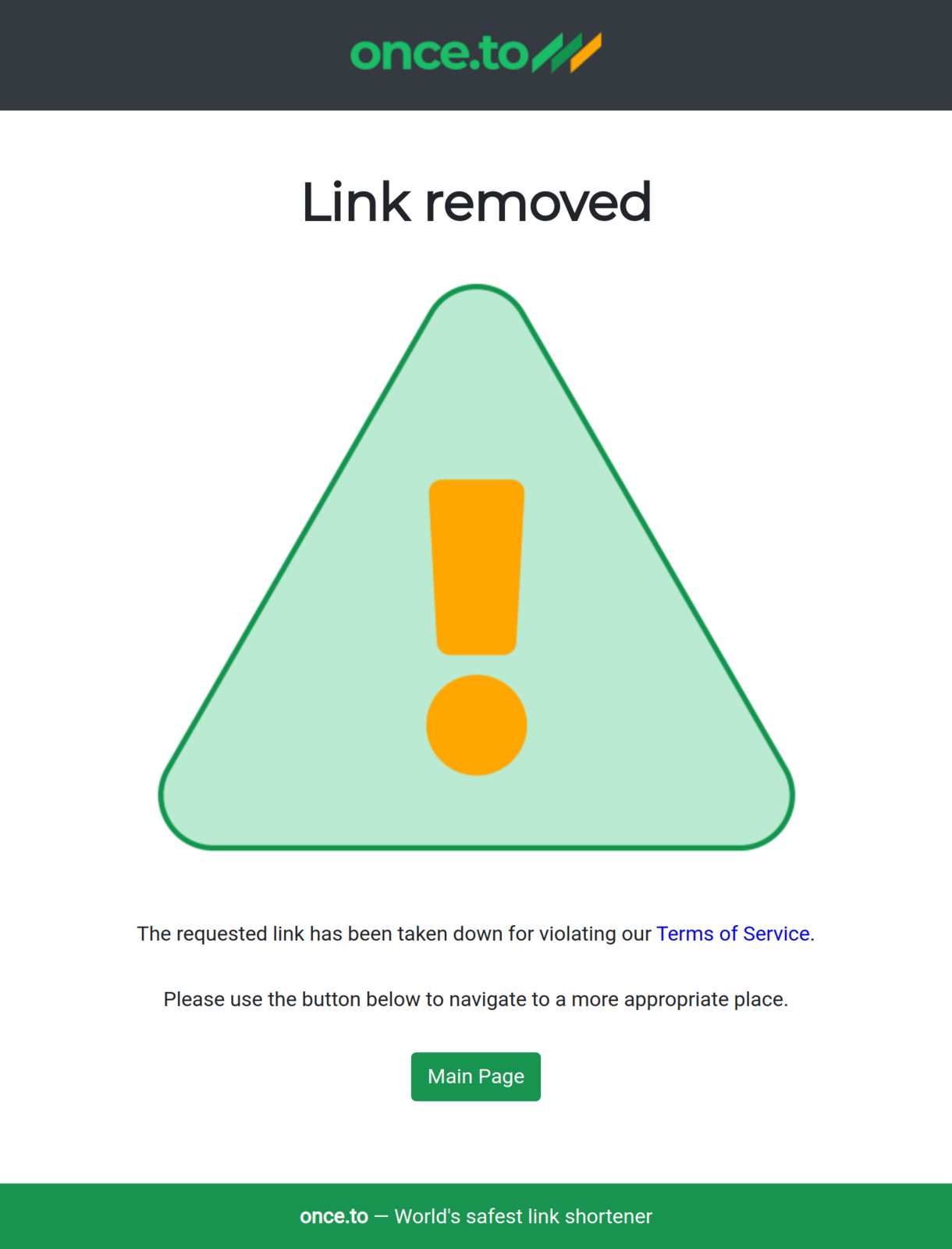
Soon there will also be a separate Abuse page, and a number of more sophisticated protective measures, which we won’t disclose just yet.
once.to is staying fully committed to security and striving to provide the safest experience to our users and visitors!
Tags: abuse, blog, cybersecurity, Google, Internet, link shortener, news, phishing, reCAPTCHA, security, spam, URL shortener, web
